2FA Authentication is implemented from version 12.0.7. onwards in Password Depot as follows:
Databases on the local system (Enterprise Server not included)
If you don't work with the Enterprise Server and simply store your databases e. g. on a local system or on one of the offered cloud services, you are able to encrypt your database either with a master password or, in addition to that, also with a key file. In this case, access to the database is only authorized when both master password and key file are correct.
Login on the Enterprise Server
The administrator is able to activate Two-Factor Authentication (2FA) by TOTP or email for the client´s server login. If you activate this feature, the client needs to enter both user name and password as well as the particular code.
If you activate e.g. TOTP, the following dialog box opens next time the client wants to log in to the Enterprise Server. The client now needs to scan the QR code with an Authenticator App.
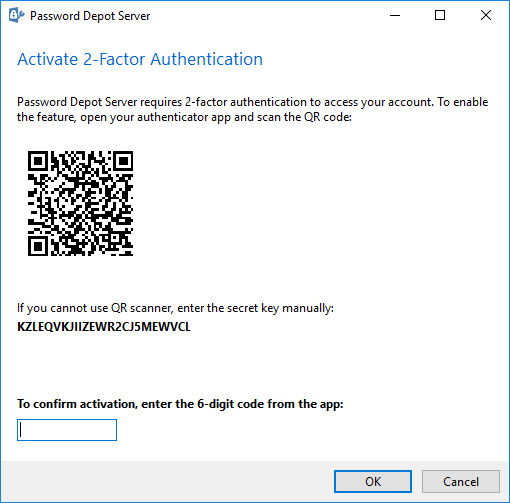
The Authenticator App must support Time-based One-Time Password algorithm (OATH TOTP) standard RFC 6238 in order to create a short living one time code.
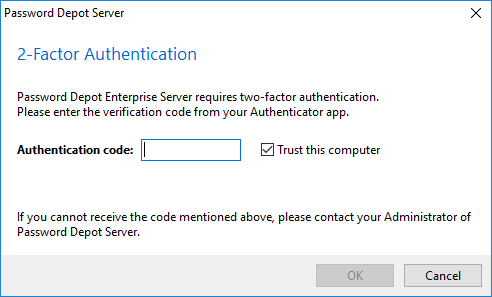
Now, users will have to enter a code each time they would like to log on to the Enterprise Server.
Technical aspects
Password Depot is working with common TOTP technology for Two-Factor Authentication (for more details, please visit https://en.wikipedia.org/wiki/Time-based_One-time_Password_algorithm). This kind of technology is not only supported by Google Authenticator but also by many other software providers such as Microsoft, Apple and others.
How does 2FA work in Password Depot?
1. If a client to whom 2FA has been assigned connects to Password Depot Enterprise Server for the first time, a unique, private key will be created by the server especially for this client and saved to the server in encrypted form.
2. Based on this shared private key, the server generates a QR code which will then be sent to the client.
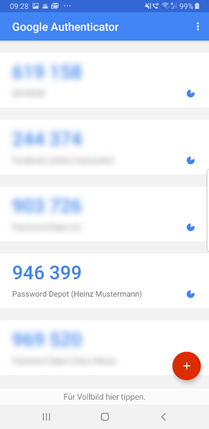
3. This code will be scanned by the client using an Authenticator App (e.g. Google, MS, Authy etc.). The client then creates a new data record in the Authenticator.
4. Next time the client is trying to establish a connection, transmission of the one-time generated 6-digit code visible in the Authenticator App will be necessary in order to connect to the server successfully.
5. At the same time, the Enterprise Server will generate the same code, too and compare it with the code it previously received from the client.
If a client is using the same computer/device permanently, it is possible to activate the option "Trust this computer" so that Password Depot Enterprise Server will remember the digital signature of this device for a specific period of time (by default, it is 30 days). During this period of time, the client will not be asked again to enter a new 2FA code on this computer. As soon as the period has expired the digital signature will be deleted by the server and it will be necessary again to use the Authenticator App if the client wants to connect to the Enterprise Server.
There is an option for resetting 2FA settings for every client in the Server Manager (e.g. if a user has lost their device or the client has been reset to its factory settings). Furthermore, supporting trusted devices and 2FA for individual clients can be deactivated, too.
Note: Two-Factor Authentication is currently available in our Windows and macOS client as well as our mobile apps (Android/iOS). Additionally, you can also use 2FA with our web client.
Comments
Please sign in to leave a comment.